ICO Ideal Data Memory (IDM) - a platform for storing information with the encryption algorithm SIZE.
Introduction
Blockchain technology has the ability to transform traditional business, it can eliminate large amounts of accounting, save money and improve IT solutions. Blockchain is a fundamental technology that can be implemented by any company to improve its economic, social or technical system.
Blockchain will create a world where every interaction between people and companies can be embedded in a digital code and stored in it. This process is transparent, safe and secure. Verified digital records and signatures will be preserved, which eliminates the need for intermediaries in this process.
Blockchain is useful because it removes the governing body by decentralizing the process. It is a peer-to-peer network with a distributed server, where information is exchanged between disparate parties. Each user is an administrator. This type of technology is useful for speeding up processes, reducing costs and increasing efficiency.
Blockchain stores data using mathematical and program rules that provide security for users. Each transaction that has ever been made on a block chain can be found in the blockroom. Each transaction has a unique cryptographic fingerprint and a key that is transmitted every time a data exchange agreement is made. Each transaction must be agreed before it is recorded, and it is encrypted and linked. Blockchain is able to help the industry, where data is very confidential and where data need to be protected.
Blockchain allows you to conduct fast and economical transactions without the need for intermediaries and high costs. Ensuring that transactions can be authenticated and verified is simplified by the chain, as everything can be traced.
Today, users daily provide and share their data with online applications to use free services from them, some examples are Facebook, Google, LinkedIn and much more. Analyst firms use the data of large online companies that store them, which often leads to a violation of the anonymity of the data. Blockchain prevents this, because each request for information must be verified by the data creator.
Now let's talk about how IDM uses the technology of blocking.

about the project
Ideal Data Memory (ideal for data storage) is a platform that provides secure data storage and decentralized data exchange for projects that are of greatest value to potential investors or investors.
At the present time there is a risk of data loss, because they are stored on the hard drive, which have the property of "crumbling" over time and are subject to wear and tear. Your data can be destroyed, or stolen by hackers
IDM is a project that solves the problem of data storage. This system is based on such a wonderful and reliable technology as blockchain, it ensures that your data will not be lost anywhere, because they are not stored centrally. In addition, the main task of the company is to take care of the security of user data, therefore, a serious and up-to-date technology such as SIZE is used, which achieves the highest possible level of protection. Previously, all this was not available, but now thanks to IDM everything is real.
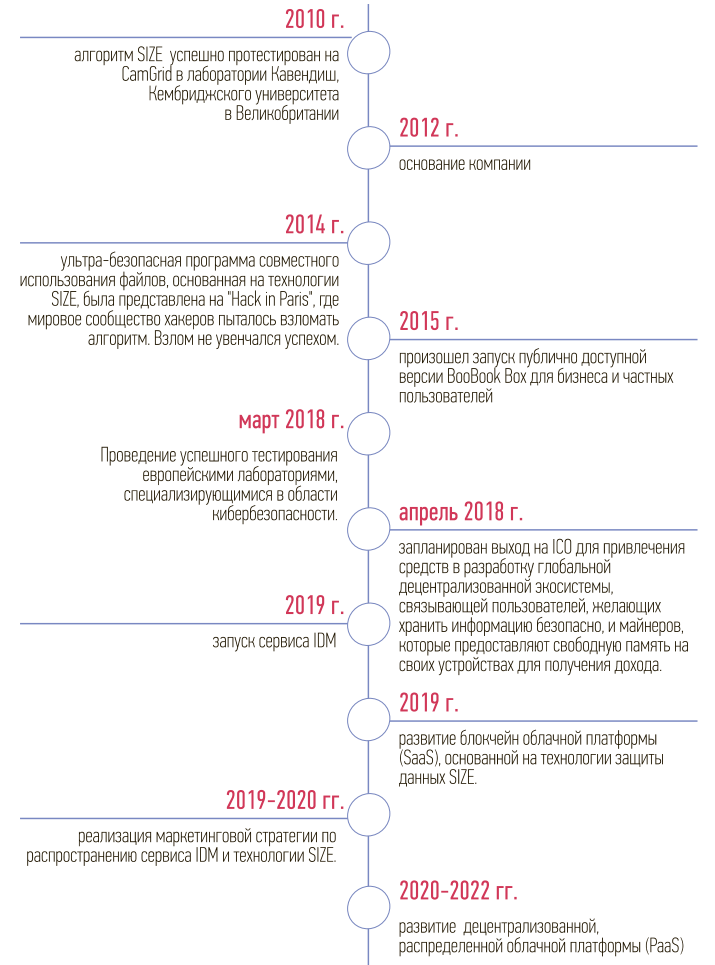
The IDM team created a working prototype of the cloud storage service called BoobookBox. The service is already operational in 2015 and has more than 2 thousand regular customers. A working prototype was launched to test and test the functionality of this technology by both developers and third parties.
How does the platform work?
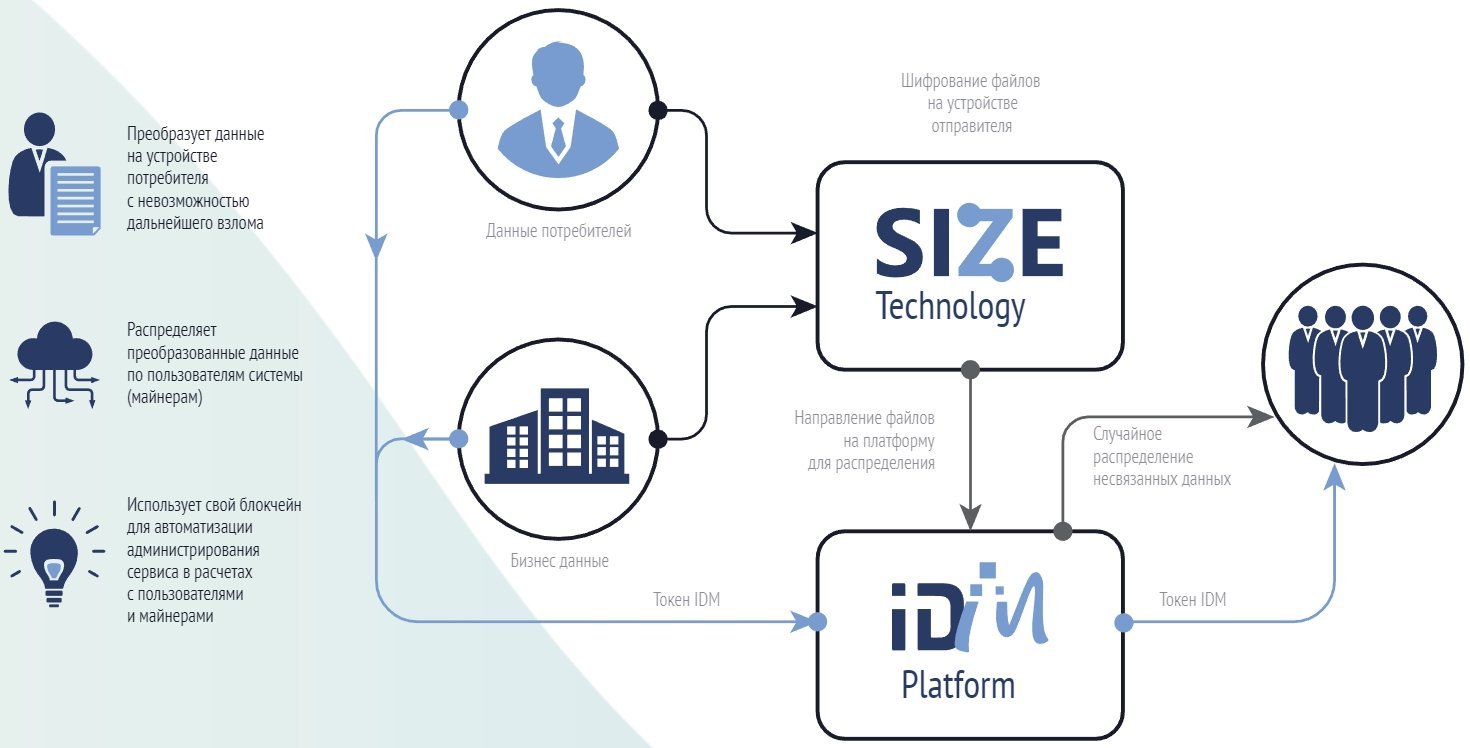
In the decentralized ecosystem of the platform, there are two groups of participants:
- Users who want to store information securely and reliably
- Miners who provide memory for their devices to generate revenue.
- According to IDM, the profitability of the miners will be about $ 5 per month for 50 GB.

SIZE encryption algorithm
Without the consent of the owner of the information, neither external persons nor employees of companies that provide information storage services in data centers or cloud services, in any public or non-governmental organizations should not have access to stored information. Usually, the encryption method is used to protect information. But this technology has its drawbacks, using the key at one stage of the transformation as a secret component.
SIZE technology automatically creates a metafile while processing the source file, which can be considered a "key" in a cryptographic sense. This "key" is created only once and never repeats. Even if the same file is converted several times using SIZE technology, a new "key" will be created each time. The conversion process itself is determined not by the "key", but by the program parameters chosen by the user in a random way. Since this is not a "cryptographic key" that is installed randomly, but a number of unrelated program settings, there is no strict binding to the truth of a random sequence. It is enough to use reliable generators of cryptographic random numbers.
The so-called "cryptographic key" is not stored anywhere, nobody is transferred, and there is no need to store a library of these "keys". Protected information can always be read, knowing the settings of the computer program, which are stored in a metafile, the base value of which does not exceed hundreds of bytes. The SIZE algorithm automatically fulfills the requirement of ensuring the authenticity and integrity of the protected information, since any change to the file results in a change in the corresponding metafile. A meta file is not a "key," it's just a file describing how the package was created.
Thus, the cryptographic key as such does not exist. And, as a result, there is no object for hacking for a quantum computer. The SIZE algorithm automatically fulfills the requirement of ensuring the authenticity and integrity of the protected information, since any change to the file results in a change in the corresponding metafile. A meta file is not a "key," it's just a file describing how the package was created. Thus, the cryptographic key as such does not exist. And, as a result, there is no object for hacking for a quantum computer.
The SIZE algorithm automatically fulfills the requirement of ensuring the authenticity and integrity of the protected information, since any change to the file results in a change in the corresponding metafile. A meta file is not a "key," it's just a file describing how the package was created. Thus, the cryptographic key as such does not exist. And, as a result, there is no object for hacking for a quantum computer.
So, let's highlight the advantages that the platform has with the use of SIZE and Blockchain technologies:
- Data stability. Even if 98% of the information is lost, the platform will restore it from the remaining 2%;
- The platform distributes the data randomly between the miners and uses the patented SIZE encryption algorithm, which ensures their reliable protection;
- The information does not go to the Internet, but is stored by the miners on personal devices;
- Resistant to hacker attacks (DDoS, etc.), even if the attack will occur from a quantum computer;
- Decentralization of the platform, which eliminates data leakage.
In 2014, SIZE, was presented at "Hack in Paris", where the world community of hackers tried to crack the algorithm. Hacking failed.
I quote one of the participants of this event:
"There was an interesting story with the Swiss company Equivalence AG. They challenged the hackers participating in the conference and handed out flyers in the form of 500 €, with an offer to open their archive."
At some point, the event de facto stopped The huge hall with the speakers bumped into their laptops, trying to solve the secret, but they were not hacked by anyone. "
Command


Road map
Tokens
All mutual calculations in the ecosystem are made in IDM tokens. The user charges for the service using tokens. A smart contract calculates the number of tokens needed to pay for leased memory, and accepts payment. The reward for miners is calculated in the same way in IDM tokens. A smart contract calculates the time period and the amount of memory leased and paid for miners.

Conclusion
The product itself already exists since 2015, the patented technology SIZE is unique in its kind, very reliable and greatly superior to the AES 256 encryption. The team includes well-known people such as Iskendera Syrgabekova and Erkin Zadula, who are known in the academic sphere of the Russian Federation. They have developed the SIZE algorithm. Confidence in the number of patents received by developers! You can see them by clicking on the link:
My forecast is very positive in terms of long-term investments. But of course you will make the decision.
If you are interested in investing, then I advise you to study in more detail the information on the links below.
References
Bitcointalk Profile ( Mulyo83 ) : https://bitcointalk.org/index.php?action=profile;u=1813751

Comments
Post a Comment